| Line 25: | Line 25: | ||
<li>In the '''Identity Provider''' view, click '''Download Metadata''' to obtain a copy of the IDP metadata XML.</li> | <li>In the '''Identity Provider''' view, click '''Download Metadata''' to obtain a copy of the IDP metadata XML.</li> | ||
<li>Employing [https://developers.onelogin.com/saml SAML] for SSO requires two parts, a Service Provider and an Identity Provider. Your Service Provider is already configured by the Genesys Auth team for you. To complete your Salesforce Identity Provider configuration, you must upload the IDP metadata XML file you created in step 1 to Agent Setup (refer to the [[Documentation:PSAAS:Administrator:SAML|Agent Setup SSO article]]).</li> | <li>Employing [https://developers.onelogin.com/saml SAML] for SSO requires two parts, a Service Provider and an Identity Provider. Your Service Provider is already configured by the Genesys Auth team for you. To complete your Salesforce Identity Provider configuration, you must upload the IDP metadata XML file you created in step 1 to Agent Setup (refer to the [[Documentation:PSAAS:Administrator:SAML|Agent Setup SSO article]]).</li> | ||
| + | <li>Open the IDP Metadata XML file in an XML viewer and find the '''Location''' parameter. You will need this parameter for the Entity ID and the ACS URL when you define Gplus Adapter as a Connected App in Salesforce. The '''Location''' URL will look something like this: <tt><nowiki>https://gws-usw1.genhtcc.com/auth/v3/saml/SingleLogout/alias/<string representing the Entity ID></nowiki></tt>.</li> | ||
</ol> | </ol> | ||
{{AnchorDiv|ConnectedApp}} | {{AnchorDiv|ConnectedApp}} | ||
| Line 39: | Line 40: | ||
</li> | </li> | ||
<li>Under Web App Settings, select '''Enable SAML''' and then provide the following: | <li>Under Web App Settings, select '''Enable SAML''' and then provide the following: | ||
| − | |||
<ul> | <ul> | ||
| − | <li>Entity ID | + | <li>Entity ID: The long string of numbers and letters at the end of the '''Location''' parameter URL after the last "/". </li> |
| − | <li>ACS URL | + | <li>ACS URL: The URL from the '''Location''' parameter that you obtained from the IDP Metadata in step 3 of the Enable Salesforce as an Identity Provider procedure.</li> |
</ul> | </ul> | ||
| − | [[File:Gplus_900_Salesforce_Setup_New_Connected_App_View.png|500px]] | + | [[File:Gplus_900_Salesforce_Setup_New_Connected_App_View.png|500px]] |
</li> | </li> | ||
<li>Use the [https://help.salesforce.com/articleView?id=identity_provider_error_log.htm&type=5 identity provider event log] to troubleshoot errors when trying to log in to Gplus Adapter.</li> | <li>Use the [https://help.salesforce.com/articleView?id=identity_provider_error_log.htm&type=5 identity provider event log] to troubleshoot errors when trying to log in to Gplus Adapter.</li> | ||
Revision as of 17:20, August 6, 2019
Contents
Single sign-on (SSO) integration to connect Gplus Adapter with Salesforce identity provider
You can simplify your agent log in process by integrating Gplus Adapter with Salesforce to use Salesforce as your single sign-on (SSO) identity provider (IDP). This means that your agent only has to provide their Username and Tenant to log in to Gplus Adapter after they have logged into Salesforce using Salesforce as your SSO identity provider. This is the general workflow when Gplus Adapter initiates the login process and uses Salesforce to identify the user:
- An agent logs in to Salesforce.
- The agent provides their Username and Tenant name in Gplus Adapter and clicks Next.
- GPlus Adapter sends a request to Salesforce to authenticate the user.
- Salesforce identifies the agent specified in the request and sends an authentication response.
- Gplus Adapter authenticates the response sent by Salesforce.
- If the agent is authenticated, they are logged in to Gplus Adapter while logged in to Salesforce.
Follow these steps to set up SSO with Salesforce as the identity provider:
Important
SSO is applicable to both test and production environments. Genesys recommends that you test SSO in your testing environment before using it in a production environment.Enable Salesforce as an Identity Provider
Prerequisites
- You must have an Admin role in your organization's Salesforce account
- User email addresses must be the same in both Salesforce and Gplus Adapter
Enable Salesforce as an Identity Provider
- Follow the steps in the Enable Salesforce as an Identity Provider article in the Salesforce Help.
- In the Identity Provider view, click Download Metadata to obtain a copy of the IDP metadata XML.
- Employing SAML for SSO requires two parts, a Service Provider and an Identity Provider. Your Service Provider is already configured by the Genesys Auth team for you. To complete your Salesforce Identity Provider configuration, you must upload the IDP metadata XML file you created in step 1 to Agent Setup (refer to the Agent Setup SSO article).
- Open the IDP Metadata XML file in an XML viewer and find the Location parameter. You will need this parameter for the Entity ID and the ACS URL when you define Gplus Adapter as a Connected App in Salesforce. The Location URL will look something like this: https://gws-usw1.genhtcc.com/auth/v3/saml/SingleLogout/alias/<string representing the Entity ID>.
Define Gplus Adapter as a Connected App in Salesforce
- To create a new Connected App follow the instructions in the Salesforce Help Defining Service Providers as SAML-Enabled Connected Apps document.
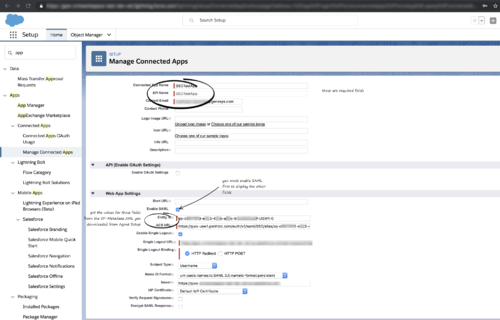
- Specify the required fields under Basic Information:
- Connected App Name (for example, Gplus Adapter)
- API Name (for example, GWS)
- Contact email (the email address of the Admin user)
- Under Web App Settings, select Enable SAML and then provide the following:
- Entity ID: The long string of numbers and letters at the end of the Location parameter URL after the last "/".
- ACS URL: The URL from the Location parameter that you obtained from the IDP Metadata in step 3 of the Enable Salesforce as an Identity Provider procedure.
- Use the identity provider event log to troubleshoot errors when trying to log in to Gplus Adapter.
Useful links
Comments or questions about this documentation? Contact us for support!