(Update with the copy of version: draft) |
|||
| Line 48: | Line 48: | ||
|- | |- | ||
| Gplus Adapter Salesforce | | Gplus Adapter Salesforce | ||
| − | | | + | | Yes |
|- | |- | ||
| QM, Recording and Speech Analytics | | QM, Recording and Speech Analytics | ||
Revision as of 12:01, October 24, 2019
Single Sign-On
Contents
PureEngage Cloud supports single sign-on (SSO), which lets users access supported applications with one login. It can also be configured to use SAML 2.0 for integrations with third-party identity providers such as Okta or Google. There are many advantages to enabling SSO in PureEngage Cloud—for example:
- Users need to remember only one password.
- User credentials are managed by a third-party identity provider.
- Users only need to log in once to gain access to PureEngage Cloud applications that have SSO enabled and non-Genesys applications that use the same identity provider.
SSO support by application
[+] Click here to see which PureEngage Cloud applications support SSO.
SSO Configuration - PureEngage Cloud
To enable Single Sign-On for your environments, see the configuration help in Agent Setup.
If you're planning to enable SSO, consider the following conventions for creating users:
- The domain declared in the identity provider metadata should be part of the user name stored within Genesys, to create the most seamless experience. (Example: john@mycompany.com) Otherwise, users would need to enter a Tenant or enter the domain before their username. (Example: mycompany\john)
- The username provisioned within PureEngage Cloud should match the username in the external identity provider.
SSO Configuration - Identity Provider
PureEngage Cloud must be defined as an application within the identity provider to support the SSO integration. Specific details for uploading PureEngage Cloud metadata and configuring claims will be published soon, but are available now by contacting your Genesys representative. Identity providers currently supported include:
- Okta
How does SSO work for users?
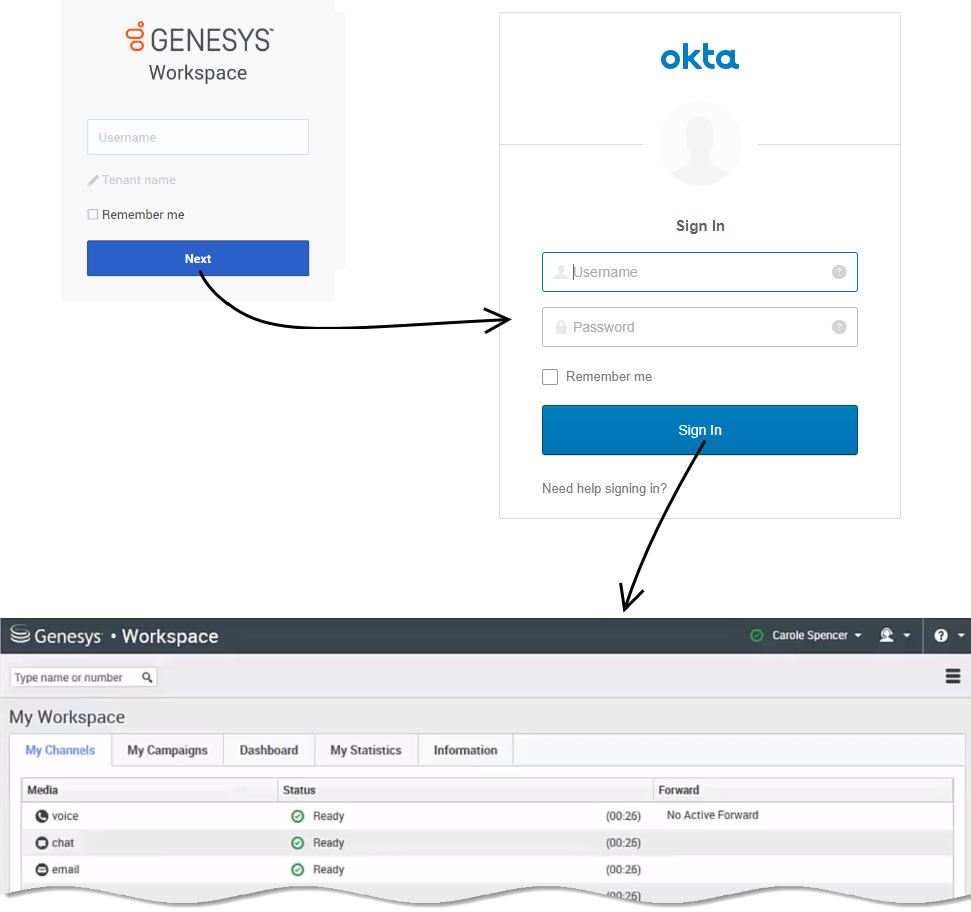
Let's look at the login process for Agent Desktop with SSO enabled and Okta configured as the third-party identity provider. Note: The login flow is the same for all supported identity providers.
First, click the Agent Desktop icon in Genesys Portal and enter your username. You must log in to the application even though you're already logged in to your workstation.
Click Next. Genesys redirects you to Okta where you're prompted to enter your username and password. Once you log in with Okta, you're redirected back to Agent Desktop and automatically logged in. Alternatively, if you are already logged in with Okta when you click Next, Genesys skips the Okta login and automatically logs you in to Agent Desktop.
Now that you're authenticated with the identity provider, you can choose any SSO-enabled application from Genesys Portal and you'll be automatically logged in without entering your credentials.
If you happen to close all browser tabs without logging out of the applications, you will remain logged in for five minutes. If a second window or browser is opened after five minutes, to either the same application or any other SSO-enabled application, you will once again be prompted for your credentials.