(Update with the copy of version: draft) |
(Update with the copy of version: draft) |
||
| Line 1: | Line 1: | ||
| − | = Single Sign-On = | + | = Enable Single Sign-On = |
Single Sign-On (SSO) identity authentication enables your users to securely access multiple Genesys applications with a single credential. | Single Sign-On (SSO) identity authentication enables your users to securely access multiple Genesys applications with a single credential. | ||
| − | After entering their username in the application login screen, users are taken to your company's authentication provider where they will enter their username and password. After that, they will not have to log in again until your authentication expires which is typically every eight hours. | + | After entering their username in the application login screen, users are taken to your company's authentication provider where they will enter their username and password. After that, they will not have to log in again until your authentication expires which is typically every eight hours. For a list of PureEngage Cloud applications supporting SSO, see [[Documentation:PSAAS:Administrator:SingleSignOn|Single Sign-On]]. |
| − | You can enable Single Sign-On for your environments in the '''SAML''' section under '''Single Sign-On'''. Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. | + | You can enable Single Sign-On for your environments in the '''SAML''' section of Agent Setup under '''Single Sign-On'''. Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. |
| + | |||
| + | |||
| + | |||
| + | {{CloudStep_Stack | ||
| + | |title=SAML fields and actions | ||
| + | |text= | ||
| + | On the SAML Configuration screen, a table displays the following information: | ||
| + | *'''Region Name''' - the name of the region in which your contact center is located. | ||
| + | *'''Base URL''' - the base URL associated with the region. This field is editable - simple double click anywhere within the text box to edit it. | ||
| + | *'''Status''' - indicates the status of configuration: | ||
| + | **'''ON''' - the configuration is complete. | ||
| + | **'''OFF''' - there is no configuration. | ||
| + | **'''PENDING''' - configuration is in progress. | ||
| + | *'''Actions''' - you take any of the following actions for a particular region: | ||
| + | ** '''Upload SAML metadata''' enables you to upload your metadata; | ||
| + | ** '''Download SAML metadata''' enables you to download SP metadata for your use. This is available after your IdP metadata has been uploaded; | ||
| + | ** '''Clear SAML metadata''' enables you to clear previously uploaded metadata in order to upload new metadata; | ||
| + | ** '''Reload SAML configuration''' refreshes the configuration for a specific region. | ||
| + | |media1=AS_SAMLtable.png | ||
| + | }} | ||
{{CloudStep_Stack | {{CloudStep_Stack | ||
| − | |title= | + | |title=Configure SAML |
|text= | |text= | ||
| − | To | + | To configure SSO: |
| + | #From the Access Groups, list, select one or more access groups. These groups contain users who will use SSO. | ||
| + | #Optional: In the '''SAML Name Identifier''' field, enter the attribute of your SAML assertion that contains the user identifier. Alternatively, you can claim this in the IdP SAML response that contains the username or external user ID. | ||
| + | #Optional: If you're using an external identification provider, select '''Use External User ID.''' | ||
| + | #Set the Base URL to the region(s). | ||
| + | #Upload the idP metadata to the region(s). | ||
| + | #Turn the '''Enable SAML''' to the '''On''' position. | ||
| + | #Click '''Save'''. | ||
| − | + | When SAML configuration completes, the status changes from PENDING to ON and the '''DownloadS AML metadata''' button is enabled. Note that for secondary regions, SAML configuration can take about 15 minutes. | |
| + | |media1=ASSAML2.png | ||
| + | }} | ||
| − | |||
| − | + | {{CloudStep_Stack | |
| + | |title=Reconfigure SAML | ||
| + | |text= | ||
| − | + | If SAML is already enabled and you need to reconfigure it with new IdP metadata, do the following: | |
| − | + | #Upload the new IdP metadata (remember: for secondary regions, SAML configuration can take up to 15 minutes). | |
| − | + | #Next, you must click the Reload SAML Configuration button. | |
| − | |||
| − | |media1= | + | |media1=AS_ReconfigureSAML.png |
}} | }} | ||
| + | |||
[[Category:V:PSAAS:Public]] | [[Category:V:PSAAS:Public]] | ||
Revision as of 18:13, November 25, 2019
Contents
Enable Single Sign-On
Single Sign-On (SSO) identity authentication enables your users to securely access multiple Genesys applications with a single credential.
After entering their username in the application login screen, users are taken to your company's authentication provider where they will enter their username and password. After that, they will not have to log in again until your authentication expires which is typically every eight hours. For a list of PureEngage Cloud applications supporting SSO, see Single Sign-On.
You can enable Single Sign-On for your environments in the SAML section of Agent Setup under Single Sign-On. Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider.
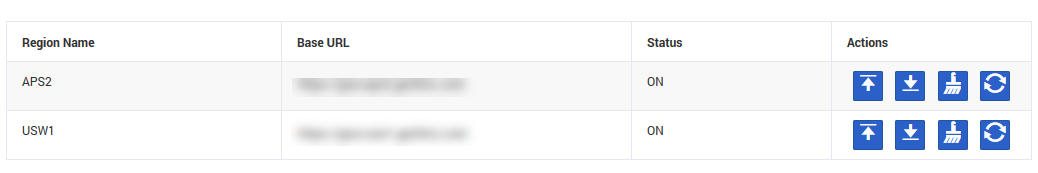
SAML fields and actions
On the SAML Configuration screen, a table displays the following information:
- Region Name - the name of the region in which your contact center is located.
- Base URL - the base URL associated with the region. This field is editable - simple double click anywhere within the text box to edit it.
- Status - indicates the status of configuration:
- ON - the configuration is complete.
- OFF - there is no configuration.
- PENDING - configuration is in progress.
- Actions - you take any of the following actions for a particular region:
- Upload SAML metadata enables you to upload your metadata;
- Download SAML metadata enables you to download SP metadata for your use. This is available after your IdP metadata has been uploaded;
- Clear SAML metadata enables you to clear previously uploaded metadata in order to upload new metadata;
- Reload SAML configuration refreshes the configuration for a specific region.
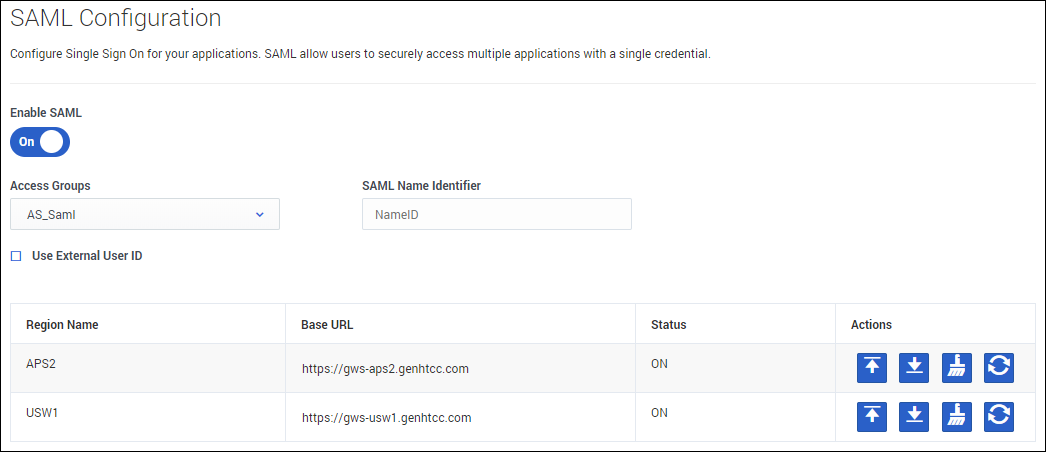
Configure SAML
To configure SSO:
- From the Access Groups, list, select one or more access groups. These groups contain users who will use SSO.
- Optional: In the SAML Name Identifier field, enter the attribute of your SAML assertion that contains the user identifier. Alternatively, you can claim this in the IdP SAML response that contains the username or external user ID.
- Optional: If you're using an external identification provider, select Use External User ID.
- Set the Base URL to the region(s).
- Upload the idP metadata to the region(s).
- Turn the Enable SAML to the On position.
- Click Save.
When SAML configuration completes, the status changes from PENDING to ON and the DownloadS AML metadata button is enabled. Note that for secondary regions, SAML configuration can take about 15 minutes.